FOCUS FRIDAY: THIRD-PARTY RISKS IN SAMBA SERVER, ATLASSIAN JIRA, TP-LINK OMADA, MINIO, SQUID PROXY, AND SAUTER EY-MODULO VULNERABILITIES
Written by: Ferdi Gül
Contributor: Hakan Karabacak
Welcome to this week’s Focus Friday, where we take a closer look at some of the most impactful vulnerabilities disclosed across critical technologies—each carrying significant third-party risk implications.
This edition examines a wide range of issues: a remote code execution flaw in Samba Server, multiple high-severity vulnerabilities in Atlassian Jira, command injection flaws affecting TP-Link Omada Gateways, a privilege escalation weakness in MinIO, a credential exposure bug in Squid Proxy, and a suite of critical vulnerabilities impacting Sauter EY-modulo building automation devices.
Together, these vulnerabilities highlight how weaknesses across network infrastructure, cloud systems, and operational technology environments can amplify third-party risk exposure.
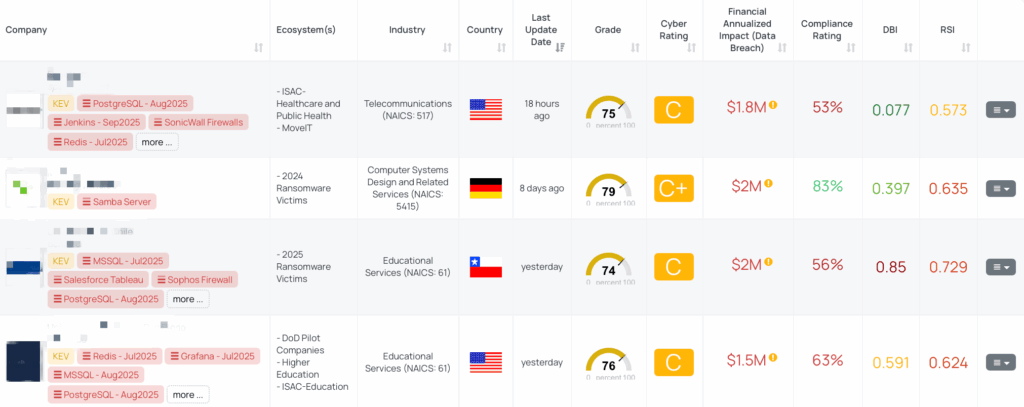
CVE-2025-10230: Samba Active Directory Domain Controller WINS RCE Vulnerability
What is the Samba Active Directory WINS “wins hook” command-injection vulnerability?
Samba, when used as an Active Directory Domain Controller (AD DC) with WINS support enabled and a wins hook parameter configured, is vulnerable to an unauthenticated remote code execution (RCE).
The WINS server component of Samba, which handles NetBIOS name-registration and name-change requests, fails to properly validate names passed to the configured “wins hook” executable. The names are concatenated into a shell command and executed — allowing a remote attacker to inject shell metacharacters in the name and execute arbitrary commands on the host.
Key technical details:
- Only affects domain controllers with Samba versions since 4.0 configured with wins support = yes and wins hook = <executable> (non-default, legacy configuration).
- The default Samba setup (wins support = no) is unaffected.
- CVSS v3.1 score: 10.0 (Attack Vector: Network, Attack Complexity: Low, Privileges Required: None, User Interaction: None).
- EPSS (Exploit Prediction Scoring System) score: 0.02%.
- Public disclosure: October 15, 2025.
- Exploitation in the wild: There is no publicly confirmed campaign or inclusion in CISA’s Known Exploited Vulnerabilities (KEV) catalog at this time.
- Workarounds and patches: Samba security advisory provides patched versions 4.23.2, 4.22.5, 4.21.9.
Why should TPRM professionals care about this vulnerability?
From a third-party risk management (TPRM) perspective, this vulnerability presents meaningful risk to vendor ecosystems where vendors use Samba as an Active Directory Domain Controller, particularly in Linux/Unix hybrid environments.
- A compromised domain controller offers an attacker high leverage: unauthorized access to directory services, lateral movement, credential harvesting, deployment of ransomware, or exfiltration of sensitive information.
- Vendors may ignore legacy features such as WINS support and “wins hook” because these are rare, but if one vendor has it enabled, a compromise could impact your supply chain via trusted vendor relationships, vendor-managed infrastructure, or hosted identity services.
- TPRM questionnaires often screen for “Are legacy protocols disabled?” or “Is WINS support used?” – but this vulnerability highlights that even unusual configurations matter.
- Because the vulnerability is high severity (10.0) yet affects a narrow configuration, it’s efficient to use vendor-scoping intelligence (such as the FocusTag) to narrow which vendors actually need to be asked, reducing vendor questionnaire fatigue and workload.
What questions should TPRM professionals ask vendors about this vulnerability?
To evaluate vendor exposure and response, you can ask the following targeted questions:
- Have you upgraded your Samba installations to the security releases 4.23.2, 4.22.5, or 4.21.9, or applied the available patches to mitigate the risk of CVE-2025-10230?
- Can you confirm if you have disabled WINS support by setting `wins support = no` in the `smb.conf` of your Samba Active Directory Domain Controllers to prevent the exploitation of CVE-2025-10230?
- Have you reconsidered the usage of the ‘wins hook’ parameter on your domain controllers, and if it must be present, have you explicitly set `wins hook =` (an empty value) to prevent command execution and mitigate the risk of CVE-2025-10230?
- Can you confirm if you have removed or avoided setting the ‘wins hook’ parameter in the `smb.conf` configuration file of your Samba Active Directory Domain Controller to prevent the exploitation of CVE-2025-10230?
Remediation recommendations for vendors subject to this risk
Vendors with affected Samba AD DCs should implement the following measures:
- Immediately upgrade Samba AD Domain Controllers to one of the patched versions: 4.23.2, 4.22.5 or 4.21.9.
- If immediate patching is not feasible, apply the following mitigations:
- Ensure wins support = no in smb.conf for AD DCs, thereby disabling the WINS server component.
- Remove or leave the wins hook parameter unset (i.e., wins hook = ) or remove reference to any executable; do not rely on “non-executable path” workaround alone.
- Review all domain controllers for legacy WINS/NetBIOS configurations: block external access to UDP port 137 if WINS cannot be disabled immediately.
- Document and validate that no unexpected “wins hook” scripts exist and that legacy services are being phased out.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite has published a FocusTag “Samba – WINS RCE” for CVE-2025-10230, enabling customers to operationalize vendor-scoping and intelligence quickly.
- Publication date: October 17, 2025.
- The tag identifies vendors that host vulnerable Samba Active Directory Domain Controllers with WINS support enabled and a configured “wins hook.” It narrows the vendor universe to those actually exposed, rather than issuing blanket questionnaires.
- Black Kite’s intelligence also surfaces the specific assets (IP addresses and/or subdomains) associated with the vendor’s infrastructure that match the vulnerable configuration, allowing more precise remediation and verification.
- For TPRM teams: Using the FocusTag means you can generate a pre-filtered list of vendors who require follow-up, integrate the tag into vendor-monitoring dashboards, and trigger automated alerts when a vendor is flagged.
- For vendors already assessed: If they have no Samba AD DCs with WINS hook enabled, you can safely exclude them from further urgent action and reduce vendor fatigue and resource drain.
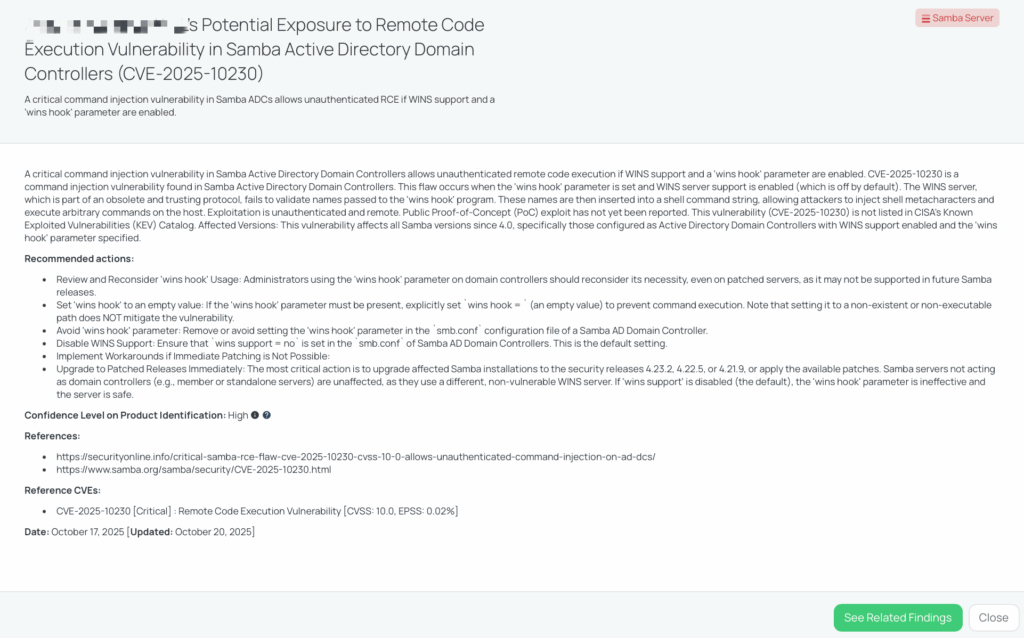
CVE-2025-22167, CVE-2025-58057, CVE-2025-58056, CVE-2025-48989, CVE-2025-7962: Atlassian Jira Family Vulnerabilities
What are the October 2025 vulnerabilities in Atlassian Jira?
Atlassian Jira Software and Jira Service Management Data Center and Server were affected by multiple vulnerabilities disclosed in October 2025. These include a Path Traversal (Arbitrary File Write) flaw (CVE-2025-22167), Denial of Service (DoS) flaws in the Netty and Tomcat dependencies (CVE-2025-58057 and CVE-2025-48989), an HTTP Request Smuggling issue (CVE-2025-58056), and an SMTP Injection flaw (CVE-2025-7962).
- CVE-2025-22167: High-severity path traversal vulnerability with a CVSS score of 8.7 and EPSS of 0.05%, allowing arbitrary file write and potential remote code execution.
- CVE-2025-58057 and CVE-2025-58056: Affect the Netty dependency, leading to denial of service or request smuggling, depending on configuration. Both were published with CVSS scores of 6.9 and 2.9 respectively, with public Proof-of-Concept exploits.
- CVE-2025-48989: The MadeYouReset DDoS flaw in Apache Tomcat’s coyote connector with a CVSS score of 7.5and EPSS 0.18%, enabling service disruption if exploited.
- CVE-2025-7962: SMTP injection flaw with a CVSS of 6.0, potentially allowing crafted input to manipulate outbound email parameters.
These vulnerabilities were published on October 21, 2025, in Atlassian’s monthly security bulletin. None of these CVEs are currently listed in CISA’s Known Exploited Vulnerabilities catalog, and no confirmed exploitation campaigns are reported.
Why should TPRM professionals care about these vulnerabilities?
From a TPRM perspective, Jira’s critical role in enterprise operations makes these vulnerabilities significant. Affected vendors using Jira could face:
- Service downtime or disruption of ticketing and workflow processes due to the DoS flaws (CVE-2025-58057, CVE-2025-48989).
- Potential data exposure or code execution from CVE-2025-22167 if attackers gain access to Jira’s filesystem.
- Email system abuse or phishing risk if SMTP injection (CVE-2025-7962) is leveraged to send malicious messages.
- Indirect risk propagation through integrated services like Confluence, Bitbucket, or CI/CD tools that depend on Jira for workflow management.
Because many third-party vendors rely on Jira for internal ticketing and vulnerability tracking, exploitation of these flaws could lead to unauthorized data modification, tampering, or service unavailability across vendor environments—ultimately impacting connected partners.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all instances of Jira Software Data Center and Server and Jira Service Management Data Center and Server to the fixed versions (e.g., Jira Software 9.12.28, 10.3.12, 11.1.0+; Jira Service Management 5.12.28, 10.3.12, 11.1.0+) to mitigate the risk of the Path Traversal flaw (CVE-2025-22167)?
- If you are using the Netty dependencies in your Jira Software Data Center or Jira Service Management Data Center, have you upgraded to the fixed versions to mitigate the risk of DoS and HTTP Request Smuggling attacks (CVE-2025-58057 and CVE-2025-58056)?
- Have you reviewed and updated your SMTP/Mail Configuration to protect against SMTP Injection (CVE-2025-7962) in mail dependencies?
- Have you implemented network segmentation or placed your Jira instances behind a Web Application Firewall (WAF) to inspect and potentially block anomalous HTTP/SOAP traffic, which can help in mitigating DoS attacks (CVE-2025-48989, CVE-2025-58057) and HTTP Request Smuggling (CVE-2025-58056)?
Remediation recommendations for vendors subject to this risk
Vendors running Jira instances should:
- Upgrade immediately to fixed versions specified in Atlassian’s October 2025 bulletin (Jira Software 9.12.28+, Jira Service Management 5.12.28+).
- Prioritize patching CVE-2025-22167 due to its arbitrary file write potential.
- Update Netty and Tomcat dependencies to patched releases to mitigate DoS and HTTP request smuggling vulnerabilities.
- Disable unnecessary mail functionality and sanitize mail input fields to prevent SMTP injection attacks.
- Segment Jira servers behind a web application firewall and restrict access to authorized networks to reduce exposure.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Atlassian Jira – Oct2025 FocusTag on October 23, 2025.
The FocusTag allows TPRM teams to identify vendors using vulnerable Jira deployments and the specific versions at risk. By correlating IPs and subdomains hosting Jira applications, Black Kite narrows vendor exposure, reducing unnecessary questionnaires.
The platform highlights whether vendors are running versions with outdated Netty or Tomcat components, providing actionable intelligence for prioritizing follow-ups.
With this FocusTag, TPRM professionals can operationalize automated vendor monitoring, focus on those with confirmed Jira exposure, and verify remediation through asset-based intelligence.
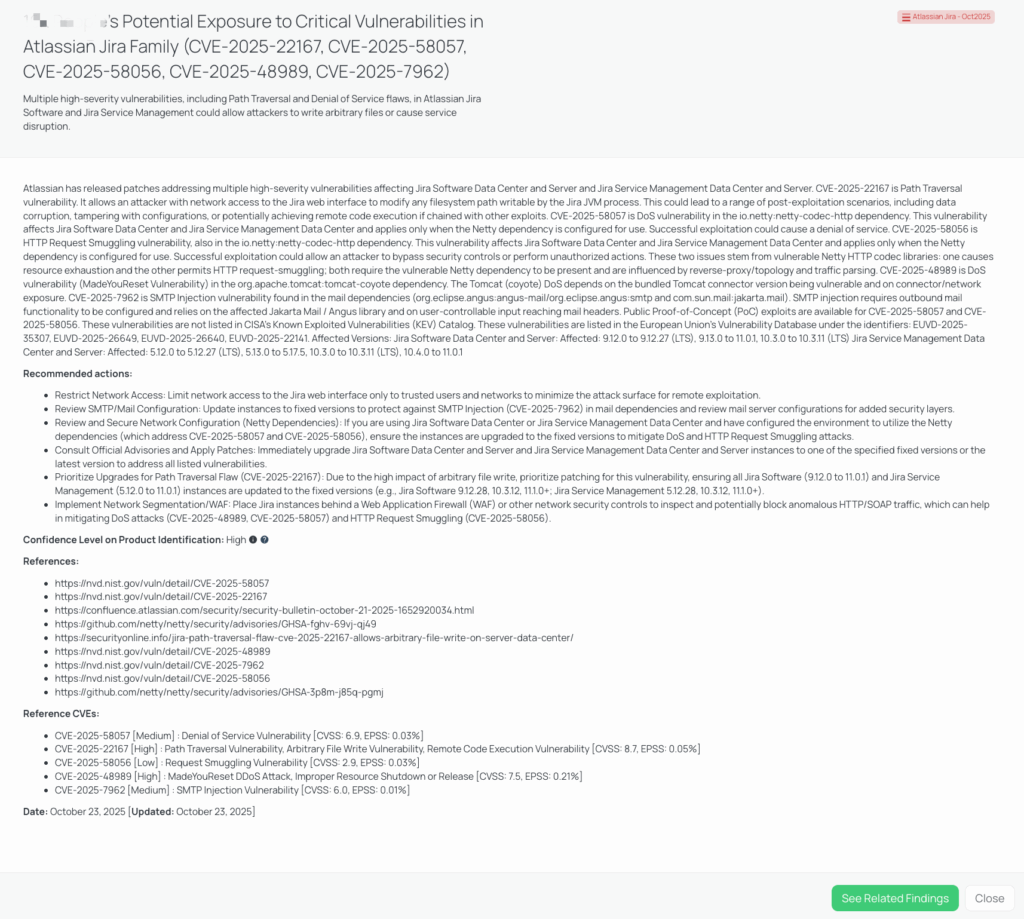
CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, CVE-2025-7851: TP-Link Omada Gateway Command Injection and Privilege Escalation Vulnerabilities
What are the TP-Link Omada OS command injection and unauthorized access vulnerabilities?
Several severe security flaws have been identified in TP-Link’s Omada series gateways. These include multiple OS command injection vulnerabilities (CVE-2025-6541, CVE-2025-6542, CVE-2025-7850) and a root privilege escalation issue (CVE-2025-7851).
- CVE-2025-6541 is a high-severity authenticated OS command injection vulnerability (CVSS: 8.6, EPSS: 0.04%) that allows logged-in users of the web management interface to execute arbitrary system commands.
- CVE-2025-6542 is a critical unauthenticated OS command injection vulnerability (CVSS: 9.3, EPSS: 0.23%) enabling remote attackers to run arbitrary commands on the device without authentication.
- CVE-2025-7850 is another critical OS command injection flaw (CVSS: 9.3, EPSS: 0.62%) allowing administrators to execute arbitrary OS commands via the web interface, potentially leading to full compromise.
- CVE-2025-7851 is a high-severity unauthorized root access vulnerability (CVSS: 8.7, EPSS: 0.02%) that stems from debug functionality left accessible in the firmware.
These vulnerabilities were disclosed on October 21, 2025, affecting multiple Omada gateway models and firmware versions. TP-Link released patched firmware to address these flaws. At this time, there are no reports of exploitation in the wild, and CISA’s KEV catalog does not include them.
Why should TPRM professionals care about these vulnerabilities?
From a TPRM perspective, these vulnerabilities pose critical risks to network infrastructure vendors and service providers who deploy TP-Link Omada gateways within managed networks.
- Exploitation of unauthenticated command injection could allow attackers to gain complete control of a gateway, monitor or reroute traffic, implant persistent malware, or pivot deeper into internal networks.
- Attackers could use compromised gateways as staging points for supply-chain intrusions, exfiltrating sensitive client or partner data.
- Because gateways often operate at the network perimeter, compromise could undermine segmentation and expose internal systems.
- Vendors providing managed networking services to multiple clients could unintentionally propagate risk if a single vulnerable device is exploited.
These vulnerabilities demonstrate how network management devices can become weak links in vendor ecosystems if not promptly updated or segmented from public access.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all instances of TP-Link Omada gateways to the specified fixed firmware versions (ER8411 >= 1.3.3 Build 20251013 Rel.44647, ER7412-M2 >= 1.1.0 Build 20251015 Rel.63594, ER707-M2 >= 1.3.1 Build 20251009 Rel.67687, ER7206 >= 2.2.2 Build 20250724 Rel.11109, ER605 >= 2.3.1 Build 20251015 Rel.78291, ER706W >= 1.2.1 Build 20250821 Rel.80909, ER706W-4G >= 1.2.1 Build 20250821 Rel.82492, and ER7212PC >= 2.1.3 Build 20251016 Rel.82571) to mitigate the risk of CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, and CVE-2025-7851?
- Have you implemented network segmentation to isolate critical network devices, including gateways, into dedicated network segments to limit the potential impact of a compromise as recommended in the advisory?
- Can you confirm if you have restricted access to the web management interface of Omada gateways to ensure it is not exposed to the public internet, and if remote management is necessary, are you using secure methods like VPNs?
- What monitoring solutions are you using to continuously monitor network traffic for any unusual activity or attempts to execute unauthorized commands on TP-Link Omada gateway devices, specifically related to potential exploitation of the OS command injection vulnerabilities?
Remediation recommendations for vendors subject to this risk
To mitigate risk, vendors should:
- Apply the latest firmware updates for all affected Omada gateways: ER8411 (≥1.3.3), ER7412-M2 (≥1.1.0), ER707-M2 (≥1.3.1), ER7206 (≥2.2.2), ER605 (≥2.3.1), ER706W and ER706W-4G (≥1.2.1), and ER7212PC (≥2.1.3).
- Restrict web management interface access to internal networks or VPN tunnels only.
- Disable debug or developer features that could permit unauthorized root access.
- Implement strict network segmentation, isolating management interfaces and preventing direct internet exposure.
- Monitor system logs and traffic for command injection attempts, unauthorized shell execution, or privilege escalation behavior.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite released the TP-Link Omada Gateways [Suspected] FocusTag on October 21, 2025, identifying vendors potentially at risk from these command injection vulnerabilities.
Through this tag, TPRM teams can:
- Detect vendors hosting IPs or subdomains linked to vulnerable Omada gateway firmware.
- Prioritize outreach to vendors operating network equipment with known vulnerable builds.
- Reduce unnecessary questionnaires by focusing only on vendors confirmed to have exposure indicators.
- Monitor updates as Black Kite refines the tag with telemetry and firmware version intelligence.
This tag enables focused, evidence-based vendor engagement, ensuring only those with measurable exposure to these gateway vulnerabilities are prioritized for remediation and validation.
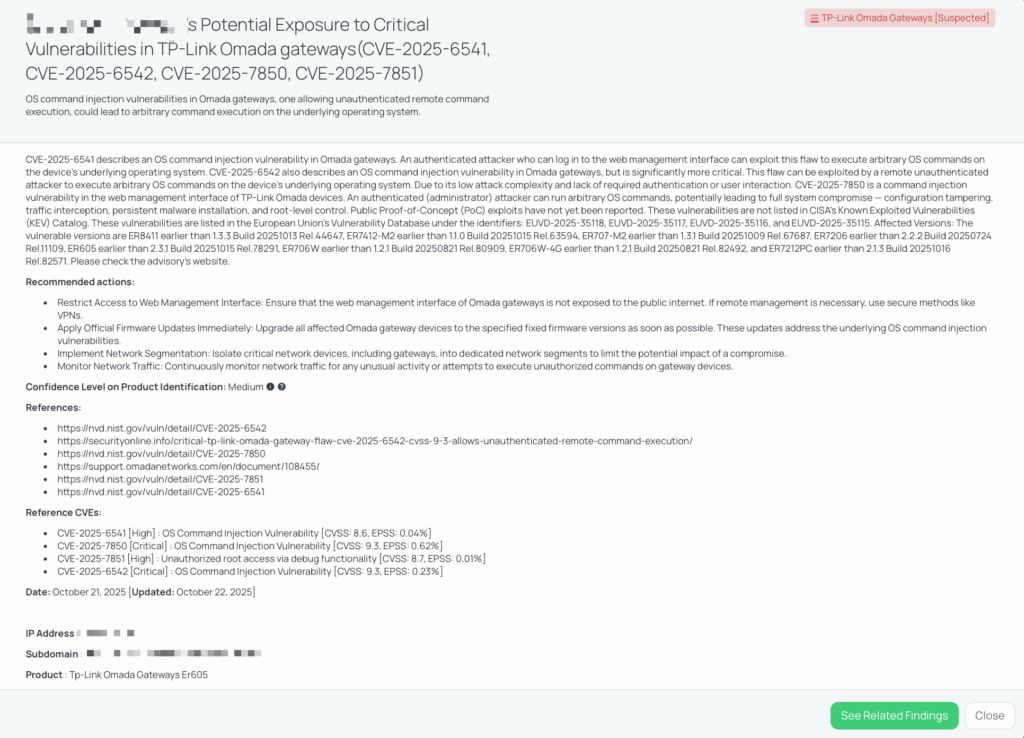
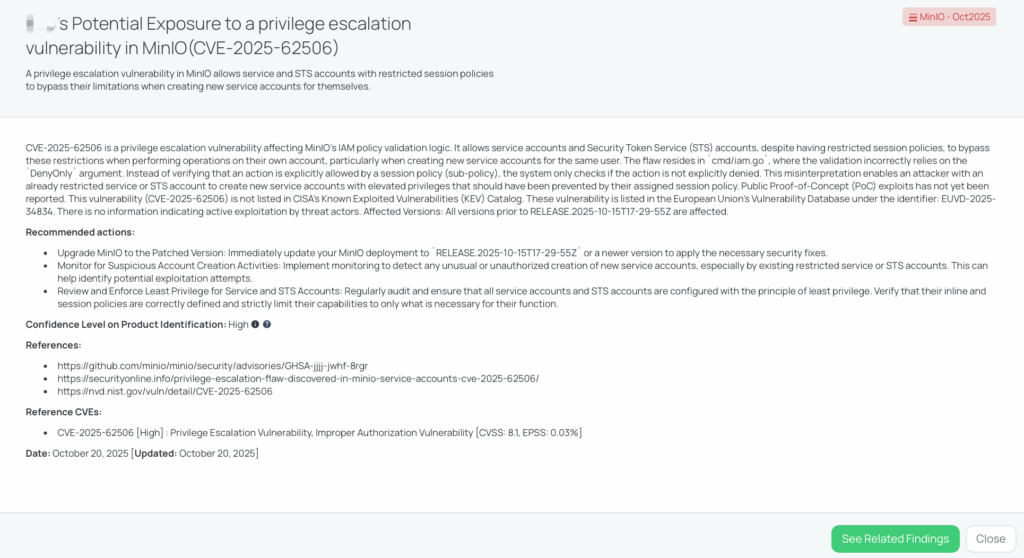
CVE-2025-62506 — MinIO Privilege Escalation (Service/STS session policy bypass)
What is CVE-2025-62506?
CVE-2025-62506 is a privilege-escalation vulnerability in MinIO’s IAM policy validation that allows service accounts and STS accounts with restricted session policies to bypass those restrictions when performing “own-account” operations (notably creating new service accounts for the same user). The flaw stems from incorrect use of a DenyOnly flag in the policy check, so the code confirms an action is not explicitly denied instead of verifying the action is explicitly allowed. Exploitation requires valid credentials for a restricted service/STS account and can result in creation of new service accounts with elevated parent privileges. Severity: High (CVSS 8.1). EPSS (as given in the FocusTag): 0.03%. Public advisory and patch were published in mid-October 2025; the fix is included in release RELEASE.2025-10-15T17-29-55Z.
Why should TPRM professionals care about this vulnerability?
From a TPRM perspective, this vulnerability exposes risks tied to data confidentiality and access control within environments that rely on MinIO for object storage. A successful exploitation could allow privilege escalation from restricted service accounts to full administrative access.
In vendor environments, this could lead to:
- Unauthorized access to sensitive customer data or proprietary information stored in object storage.
- Manipulation or deletion of backup files, artifacts, or stored credentials.
- Persistent compromise through newly created privileged service accounts.
Since MinIO often underpins cloud-native architectures, CI/CD pipelines, and internal data stores, the exploitability of this issue can significantly impact supply chain integrity and third-party data trust.
What questions should TPRM professionals ask vendors about this vulnerability?
- Have you updated your MinIO deployment to the patched version `RELEASE.2025-10-15T17-29-55Z` or a newer version to mitigate the risk of CVE-2025-62506?
- Have you implemented monitoring to detect any unusual or unauthorized creation of new service accounts, especially by existing restricted service or STS accounts, to identify potential exploitation attempts of CVE-2025-62506?
- Can you confirm that all service accounts and STS accounts are configured with the principle of least privilege and their inline and session policies are correctly defined and strictly limit their capabilities to only what is necessary for their function?
- Have you reviewed all service accounts created by non-admin accounts and deleted any service accounts that may have been created through exploitation of CVE-2025-62506?
Remediation recommendations for vendors subject to this risk
Vendors using MinIO should take the following actions:
- Upgrade immediately to RELEASE.2025-10-15T17-29-55Z or newer.
- Audit service and STS accounts to ensure none have elevated privileges or were created unexpectedly.
- Reinforce least-privilege configurations: Ensure all IAM session and inline policies are strictly defined and validated.
- Enable enhanced logging and alerts: Track service-account creation events, policy modifications, and access anomalies.
- Revoke compromised credentials and rotate keys for any accounts suspected of abuse.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s FocusTag for MinIO (published per the tag metadata in October 2025) helps TPRM teams rapidly determine which vendors are likely exposed by surfacing evidence-backed indicators: which vendors run MinIO, versions observed, and assets (IPs/subdomains) linked to vulnerable builds. That asset-level signal lets you prioritize outreach only to vendors with measurable exposure—confirm patched status, request audit evidence (upgrade logs, account-creation event history), and reduce needless questionnaires for vendors that have no MinIO footprint. Combining the FocusTag with your existing vendor scoring and automated monitoring streamlines follow-up, verification, and risk reduction.
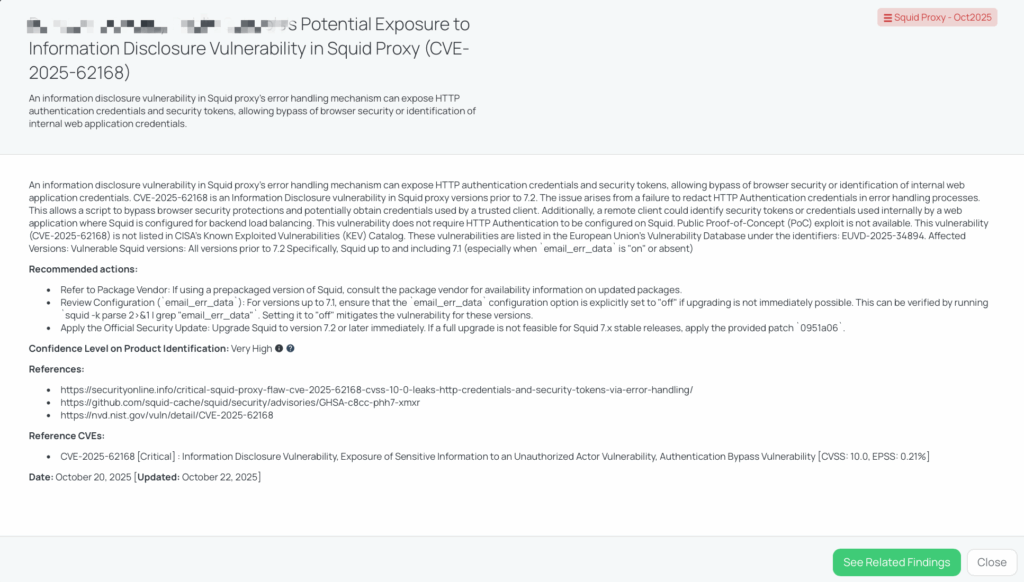
CVE-2025-62168 — Squid Proxy Information Disclosure Vulnerability
What is CVE-2025-62168?
CVE-2025-62168, also tracked as SQUID-2025:2, is a critical information disclosure vulnerability found in Squid Proxy versions prior to 7.2. The flaw arises from improper handling of HTTP Authentication data within Squid’s error-handling mechanism. Specifically, when an error is generated and returned to a client, Squid fails to redact HTTP authentication credentials or related security tokens embedded in the request headers.
This allows a malicious script or attacker-controlled client to capture sensitive information such as authentication headers, API tokens, or session identifiers. The flaw is particularly dangerous because it can occur even when Squid itself is not configured to use HTTP authentication, making exposure possible in broader deployment scenarios.
The vulnerability has a CVSS score of 10.0 (Critical) and an EPSS score of 0.21%, indicating both high severity and a measurable probability of exploitation. It was disclosed publicly in October 2025 and affects all versions prior to 7.2, particularly those where the configuration option email_err_data is set to “on” or left undefined.
As of now, there are no public Proof-of-Concept (PoC) exploits and no known exploitation in the wild. The issue is not listed in CISA’s Known Exploited Vulnerabilities (KEV) Catalog, and there are no CISA advisories related to it at the time of publication.
Why should TPRM professionals care about this vulnerability?
From a third-party risk management perspective, this vulnerability carries severe data exposure implications. Squid Proxy is often used by vendors and service providers for caching, load balancing, and secure proxying of internal web applications.
A successful exploitation could lead to:
- Disclosure of sensitive credentials used between internal services, resulting in lateral movement opportunities within a vendor’s environment.
- Exposure of tokens or session identifiers, enabling unauthorized access to applications or APIs that rely on those credentials.
- Breach of internal security boundaries, as Squid proxies often act as intermediaries between trusted and untrusted networks.
In the context of supply-chain security, if a vendor’s internal or customer-facing applications use a vulnerable Squid deployment, exposed credentials could indirectly compromise your organization’s data or access routes.
What questions should TPRM professionals ask vendors about this vulnerability?
- Can you confirm if you have upgraded all instances of Squid Proxy to version 7.2 or later to mitigate the risk of CVE-2025-62168?
- Have you reviewed the configuration of `email_err_data` for versions up to 7.1 and ensured that it is explicitly set to \”off\” if upgrading is not immediately possible?
- If you are unable to upgrade to Squid 7.2 or later, have you applied the provided patch `0951a06` to mitigate the risk of CVE-2025-62168?
- Can you confirm if you have discontinued the use of all Squid versions up to and including 7.1, especially when `email_err_data` is \”on\” or absent, to mitigate the risk of CVE-2025-62168?
Remediation recommendations for vendors subject to this risk
Vendors should immediately:
- Upgrade Squid Proxy to version 7.2 or newer, which includes the fix for CVE-2025-62168.
- If an immediate upgrade is not feasible, apply patch 0951a06 to mitigate the issue in affected stable releases.
- Set email_err_data to “off” in the Squid configuration file to prevent the exposure of credentials in error responses.
- Review internal proxy configurations and ensure no sensitive data is being relayed through error pages or client-side messages.
- Rotate exposed credentials or tokens if any were potentially logged or transmitted through affected instances.
- Consult your OS or package vendor to confirm patched versions if using a distribution-provided Squid package.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Squid Proxy – Oct2025 FocusTag on October 20, 2025, with a very high confidence level.
This FocusTag helps TPRM professionals identify vendors potentially using vulnerable Squid Proxy deployments prior to version 7.2. Using asset-based intelligence such as IPs and subdomains, Black Kite isolates vendors running Squid services that match affected versions or configurations.
Through this FocusTag, TPRM teams can:
- Prioritize vendor follow-ups where Squid assets are confirmed.
- Reduce assessment scope by excluding unaffected vendors.
- Track remediation over time as vendors patch or reconfigure affected systems.
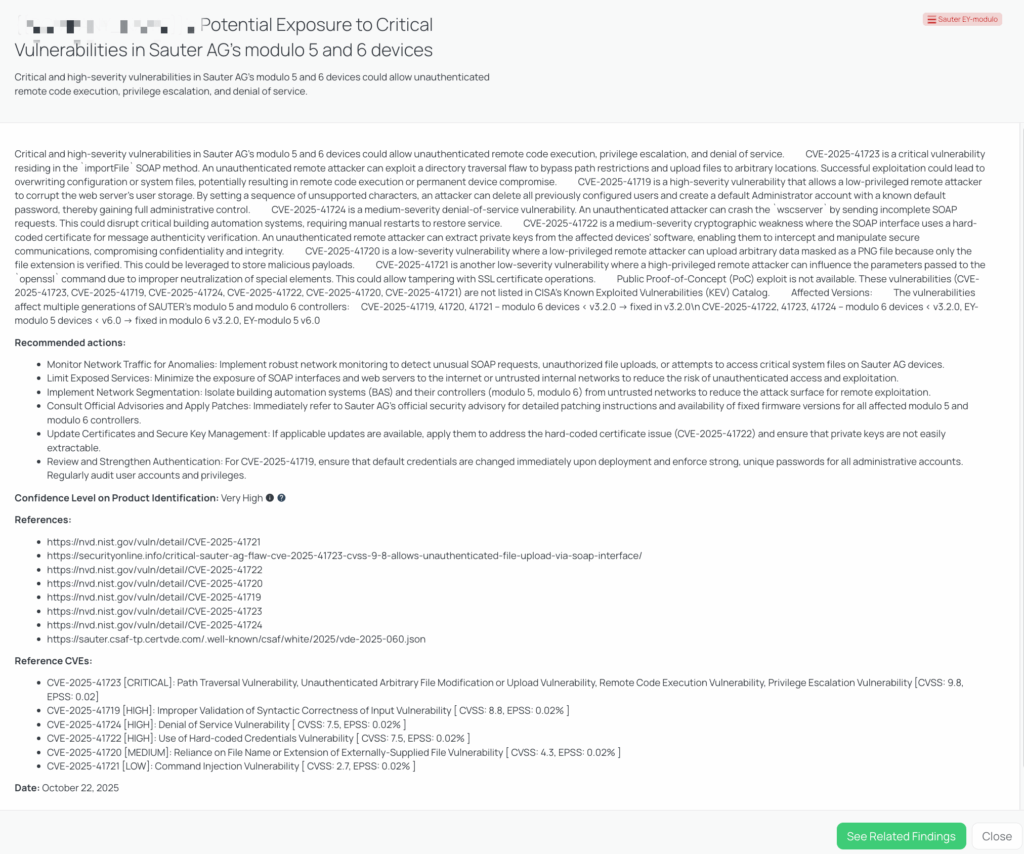
CVE-2025-41723 — Sauter (EY-modulo / modulo) Directory Traversal & Related Flaws
What is CVE-2025-41723 and the related Sauter device issues?
CVE-2025-41723 is a critical directory-traversal and unauthenticated file-upload vulnerability in Sauter AG’s EY-modulo 5 and modulo 6 product families. The flaw exists in the SOAP importFile method, allowing a remote unauthenticated attacker to bypass path restrictions and upload arbitrary files to the device’s filesystem. Successful exploitation can lead to configuration overwrites, firmware tampering, or remote code execution.
Several related vulnerabilities were also disclosed:
- CVE-2025-41719 (CVSS 8.8): Improper input validation allowing user store corruption and default admin takeover.
- CVE-2025-41724 (CVSS 7.5): Denial-of-service condition caused by incomplete SOAP requests.
- CVE-2025-41722 (CVSS 7.5): Hard-coded certificate allowing key extraction and message tampering.
- CVE-2025-41720 (CVSS 4.3): File upload based only on file extension validation.
- CVE-2025-41721 (CVSS 2.7): Weak command parameter neutralization allowing SSL tampering.
All vulnerabilities share an EPSS of 0.02% and affect both EY-modulo 5 and modulo 6 systems.
These issues were publicly disclosed in October 2025, with vendor patches released soon after. There are currently no public exploits and no evidence of exploitation in the wild, nor are they listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why should TPRM professionals care about these Sauter vulnerabilities?
Sauter’s EY-modulo and modulo devices are used in building automation systems (BAS) to control heating, ventilation, lighting, and access systems. A compromise of these systems introduces risks that extend beyond IT to physical security and operational continuity.
For third-party risk management professionals, the key considerations include:
- Remote code execution or privilege escalation can grant attackers persistent control over vendor-managed BAS systems.
- Default credential and certificate reuse can lead to compromise across multiple environments managed by the same vendor.
- Denial-of-service attacks could disable HVAC or safety systems, disrupting business operations and facility safety.
Because vendors often manage these systems remotely for multiple clients, a single exploited Sauter controller could become a supply-chain entry point, impacting multiple organizations at once.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all instances of Sauter AG’s modulo 5 and 6 devices to the fixed versions (modulo 6 v3.2.0, EY-modulo 5 v6.0) to mitigate the risk of CVE-2025-41723, CVE-2025-41719, CVE-2025-41724, CVE-2025-41722, CVE-2025-41720, and CVE-2025-41721?
- Can you confirm if you have implemented robust network monitoring to detect unusual SOAP requests, unauthorized file uploads, or attempts to access critical system files on Sauter AG devices, specifically related to potential exploitation of the `importFile` SOAP method (CVE-2025-41723)?
- Have you addressed the hard-coded certificate issue (CVE-2025-41722) by applying available updates and ensuring that private keys are not easily extractable?
- Can you confirm if you have taken measures to strengthen authentication, such as changing default credentials immediately upon deployment and enforcing strong, unique passwords for all administrative accounts, to mitigate the risk of CVE-2025-41719?
Remediation recommendations for vendors subject to this risk
Vendors should take the following actions to mitigate the risk:
- Apply the latest firmware updates: EY-modulo 5 should be upgraded to version 6.0 or later, and modulo 6 to version 3.2.0 or later.
- Restrict access: Limit exposure of SOAP interfaces and management ports to secure networks or VPNs only.
- Enforce strong authentication: Remove default admin accounts, enforce unique strong passwords, and disable unused credentials.
- Replace static certificates: Regenerate device certificates to mitigate risks associated with hard-coded keys.
- Implement network segmentation: Isolate BAS controllers from corporate IT and external access points.
- Enable logging and monitoring: Track unusual file uploads, user resets, or SOAP requests that may indicate exploitation attempts.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Sauter EY-modulo FocusTag on October 22, 2025, with very high confidence.
This tag identifies vendors that potentially operate or host Sauter BAS devices vulnerable to these issues. Using asset-level intelligence such as IPs and subdomains, Black Kite enables:
- Targeted vendor identification, allowing teams to focus on suppliers with confirmed exposure.
- Prioritized remediation tracking, monitoring firmware version changes or removal of vulnerable devices.
- Reduced questionnaire fatigue, as only vendors with observable exposure are contacted.
MAXIMIZING TPRM EFFECTIVENESS WITH BLACK KITE’S FOCUSTAGS™
In today’s interconnected ecosystem, the ability to detect and assess emerging vulnerabilities across vendors and technologies is essential for maintaining a resilient Third-Party Risk Management (TPRM) posture. Black Kite’s FocusTags™ deliver this capability by transforming real-time vulnerability intelligence into actionable third-party insights.
- Real-Time Risk Identification: Detect vendors potentially affected by high-impact vulnerabilities—such as those recently discovered in Samba, Jira, Omada, MinIO, Squid, and Sauter systems—enabling faster, data-driven responses.
- Targeted Risk Prioritization: Align remediation priorities by mapping vulnerability severity with vendor criticality, ensuring focus on what matters most.
- Informed Vendor Engagement: Support meaningful conversations with suppliers about their security controls, patching timelines, and exposure mitigation steps related to specific vulnerabilities.
- Comprehensive Ecosystem Awareness: Provide a holistic understanding of the evolving threat landscape across IT, cloud, and OT environments.
By leveraging Black Kite’s FocusTags™, organizations can not only identify third-party exposures with precision but also strengthen their overall cybersecurity strategy—transforming complex vulnerability data into strategic, actionable intelligence for proactive third-party risk management.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- Samba Server : CVE-2025-10230, Remote Code Execution Vulnerability in Samba servers.
- Atlassian Jira – Oct2025 : CVE-2025-22167, CVE-2025-58057, CVE-2025-58056, CVE-2025-7962, CVE-2025-48989, Path Traversal, Arbitrary File Write, Remote Code Execution (RCE), Denial of Service (DoS), Request Smuggling, SMTP Injection, Improper Resource Shutdown or Release (MadeYouReset DDoS) vulnerabilities in Atlassian Jira Software and Jira Service Management.
- TP-Link Omada Gateways : CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, CVE-2025-7851, OS Command Injection vulnerabilities and Unauthorized Root Access via Debug Functionality in TP-Link Omada Gateways.
- MinIO – Oct2025 : CVE-2025-62506, Privilege Escalation Vulnerability in MinIO servers.
- Squid Proxy – Oct2025 : CVE-2025-62168, Information Disclosure Vulnerability in Squid Proxy.
- Sauter EY-modulo : CVE-2025-41723, CVE-2025-41724, CVE-2025-41722, CVE-2025-41721, CVE-2025-41720, CVE-2025-41719, Improper Validation of Syntactic Correctness of Input Vulnerability, Denial of Service Vulnerability, Use of Hard-coded Credentials Vulnerability, Reliance on File Name or Extension of Externally-Supplied File Vulnerability, Command Injection Vulnerability in Sauter EY-modulo.
- Oracle EBS: CVE-2025-61882, Remote Code Execution Vulnerability, Missing Authentication for Critical Function Vulnerability in Oracle E-Business Suite.
- Jenkins – Oct2025: CVE-2017-1000353, Remote Code Execution Vulnerability in Jenkins.
- Redis – Oct2025: CVE-2025-49844, CVE-2025-46817, CVE-2025-46818, CVE-2025-46819, Remote Code Execution Vulnerability in Redis.
- DrayTek Vigor – Oct2025: CVE-2025-49844, CVE-2025-46817, CVE-2025-46818, CVE-2025-46819, Remote Code Execution Vulnerability in DrayTek Vigor Routers.
- Zimbra – Oct2025: CVE-2025-27915, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration Suite.
- Elastic – Oct2025: CVE-2025-25009, CVE-2025-25017, CVE-2025-25018, CVE-2025-37727, CVE-2025-37728, Cross-Site Scripting (XSS) Vulnerability, Unrestricted File Upload Vulnerability, Information Disclosure Vulnerability, Insufficiently Protected Credentials Vulnerability in Elastic & Kibana.
- Django – Oct2025: CVE-2025-59681, CVE-2025-59682, SQL Injection Vulnerability, Directory Traversal Vulnerability in Django.
- Grafana – Oct2025: CVE-2021-43798, Directory Traversal Vulnerability in Grafana.
- SillyTavern: CVE-2025-59159, DNS Rebinding Vulnerability, Remote Code Execution Vulnerability, Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in SillyTavern.
- WP Yoast SEO – Oct2025: CVE-2025-11241, Cross-Site Scripting (XSS) Vulnerability in WP Yoast SEO.
- Cisco ASA – Sep2025: CVE-2025-20333, CVE-2025-20362, Buffer Overflow Vulnerability, Missing Authorization in Cisco ASA and Cisco FTD.
- Cisco ASA & FTD & IOS – Sep2025: Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in Cisco ASA, Cisco IOS, and Cisco FTD.
- VMware vCenter – Sep2025: CVE-2025-41250, SMTP Header Injection Vulnerability, Username Enumeration Vulnerability, Weak Password Recovery Mechanism Vulnerability in VMware vCenter.
- WD My Cloud: CVE-2025-30247, Command Injection Vulnerability in multiple Western Digital My Cloud network-attached storage (NAS) devices.
- Formbricks: CVE-2025-59934, Remote Code Execution Vulnerability in Formbricks.
- GoAnywhere – Sep2025: CVE-2025-10035, Deserialization Remote Code Execution Vulnerability in Fortra GoAnywhere MFT.
- SolarWinds Web Help Desk – Sep2025: CVE-2025-26399, Remote Code Execution Vulnerability in SolarWinds Web Help Desk.
- Cisco SNMP – Sep2025: CVE-2025-20352, Stack Overflow Vulnerability leading to DoS and Remote Code Execution in Cisco IOS and IOS XE Software.
- DNN Software: CVE-2025-59545, Stored Cross-Site Scripting (XSS) Vulnerability in DNN Prompt Module.
- Jetty – MadeYouReset: CVE-2025-5115, MadeYouReset DoS Vulnerability in Eclipse’s Jetty.
- Jenkins – Sep2025: CVE-2025-59474, CVE-2025-59475, CVE-2025-59476, Information Disclosure Vulnerability, Log Message Injection Vulnerability in Jenkins.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://www.samba.org/samba/security/CVE-2025-10230.html
https://nvd.nist.gov/vuln/detail/CVE-2025-22167
https://nvd.nist.gov/vuln/detail/CVE-2025-58057
https://nvd.nist.gov/vuln/detail/CVE-2025-58056
https://nvd.nist.gov/vuln/detail/CVE-2025-7962
https://nvd.nist.gov/vuln/detail/CVE-2025-48989
https://github.com/netty/netty/security/advisories/GHSA-3p8m-j85q-pgmj
https://github.com/netty/netty/security/advisories/GHSA-fghv-69vj-qj49
https://confluence.atlassian.com/security/security-bulletin-october-21-2025-1652920034.html
https://support.omadanetworks.com/en/document/108455/
https://nvd.nist.gov/vuln/detail/CVE-2025-6541
https://github.com/minio/minio/security/advisories/GHSA-jjjj-jwhf-8rgr
https://nvd.nist.gov/vuln/detail/CVE-2025-62506
https://github.com/minio/minio/security/advisories/GHSA-jjjj-jwhf-8rgr
https://nvd.nist.gov/vuln/detail/CVE-2025-62506
https://github.com/squid-cache/squid/security/advisories/GHSA-c8cc-phh7-xmxr
https://nvd.nist.gov/vuln/detail/CVE-2025-62168
https://sauter.csaf-tp.certvde.com/.well-known/csaf/white/2025/vde-2025-060.json
https://nvd.nist.gov/vuln/detail/CVE-2025-41724
https://nvd.nist.gov/vuln/detail/CVE-2025-41723
https://nvd.nist.gov/vuln/detail/CVE-2025-41722
https://nvd.nist.gov/vuln/detail/CVE-2025-41721

